#Web Scraping Techniques
Explore tagged Tumblr posts
Text
Lensnure Solutions is a passionate web scraping and data extraction company that makes every possible effort to add value to their customer and make the process easy and quick. The company has been acknowledged as a prime web crawler for its quality services in various top industries such as Travel, eCommerce, Real Estate, Finance, Business, social media, and many more.
We wish to deliver the best to our customers as that is the priority. we are always ready to take on challenges and grab the right opportunity.
3 notes
·
View notes
Text
#proxies#proxy#proxyserver#residential proxy#automation#ecommerce#data insights#data intеgration challеngеs#web scraping techniques#web scraping services#web scraping tools#industry data#datascience#data analytics#market analysis#shopping
0 notes
Video
youtube
urllib.error.HTTPError: HTTP Error 403: Forbidden | Python web scraping
0 notes
Text
youtube
GPT-4 Vision API + Puppeteer = Easy Web Scraping
In today's video I do some experimentation with the new GPT-4 Vision API and try to scrape information from web pages using it.
#education#free education#youtube#gpt 4#chat gpt#gpt4#gpt 4 ai technology#gpt#artificial intelligence#ai#tech#chatgpt#web scraping techniques#web scraping tools#Youtube
0 notes
Text
Learn data gathering methods for e-commerce with web scrapers. Discover techniques to extract valuable insights. Enhance your data-driven decision-making.
For More Information:-
0 notes
Text
Masterlist here
Tales the Songs Weave
Ch.11<< >>Ch.13
Notes: Miguel shows you a very important person that was in his life.
CW: Grieving/mourning
Artwork done by @/Melteyyo on Twitter

Chapter 12: Just Let My Love Adorn You
Word count: 6.3K
For the past couple of weeks, you and Miguel have been essentially inseparable. Every other night, he would sneak you into the HQ or cut his days shorter and shorter to hang out at your place or job.
Occasionally spending an hour at the botanical garden if given the chance.
Miguel's excuses started to become more noticeable and rampant as to why he couldn't be around for certain assignments or missions.
A game of telephone began when a few spiders gossiped and took bets about where their commander vanishes to; however, it escalated quite rampantly when Miguel's attitude seemed slightly less perturbed.
He would still retain those explosive moments, then promptly inhale and exhale, following it up with an actual conversation. It didn't fully waver his palpable tantrums and hostility.
He just came off as less grumpy, and that was enough to get the snowball tumbling towards the steep. Betting pools were established by the braver ones, but they were quickly shut down when Jess caught wind of that.
She finds herself at the forefront exceedingly often now, and it's been grating on her. With her new underling, keeping track of the anomalies, piles of paperwork, and basically dealing with his tasks and her pregnancy.
Needless to say, Jess wasn't in the best of moods. She interrogated Miguel at any chance she was allowed, probing on about these codes and asking about the gizmos and goobers he keeps accumulating over time.
“This project must really be something big if you need all this junk. That's what? The sixth time that you went out to get these items in the span of two weeks, and I've yet to see you actually touch them.”
Jess dryly stated, picking up some busted chips and tossing them back into the cardboard box.
“I told you, Jess, several hundred times. It takes time. I'm going to use them; now let it go all the way. I'm tired of hearing about it.” Miguel typed away, a clear indication of displeasure.
“Oh, you're tired? That's so funny, because I don't think I'm tired of asking.” She crossed her arms over her protuberant stomach.
“Jess, will you just leave it?!” He jeered at her, but she refused to back down.
“And what about that code? Gwen asked me the other day about it. When exactly will you fix the portal's jerky momentum? I would've thought there would have been some prototypes or something.”
Jess knew she was poking the beast, but at this point, all care was thrown out the window.
“And those reports. You've been falling back again after that night when I told you to help. You were doing them for three days, but then you fell right back off!”
The sounds of metal echoed in the air as Miguel scraped his desk, incarcerating the explosion that was sneaking its way out.
A young spider in a gold and green one-piece turtleneck spandex leotard, covered in webs, froze at the ear-piercing noise.
Jess and Miguel faced the spider, who apprehensively shuffled backwards.
“I think I'm distributing something; I-I'll just ask later.”
They shot out a web, swinging as fast as their webs could carry them.
“Right. Miguel, I'm tired. I AM tired. After that first day, you came back two hours late. I said that would be the only time. But I kept letting it slide, trying to give you the benefit of the doubt!”
Jess threw her hands up, marching back and forth. “Now look at where that has gotten me! I'm the fool in your circus!”
He used his breathing techniques, cursing under his breath. He's done this by himself many times. He never got a break; he barely had any. He wanted to scoff at Jess as silence pricked the cold air.
He didn't need this.
“Jeez Miguel, did you have to send us on a mission like that? I nearly busted my back in that fight!”
He didn't need this.
“Peter, we did most of the fighting. You were too busy trying to get a hold of Mayday.”
“I don't know why I let her wear that web shooter today; that was an accident.”
An elated shrill, followed by clapping, sprang from below.
He didn't need this.
“Oi, are you going to acknowledge us? I know you don't like using manners, but at least pretend to show some.”
He REALLY didn't need this.
“Hey Jess, are you talking to Miguel about the portal thing?” Gwen greeted her mentor as the older woman just turned towards Miguel, whose back was the only thing for show.
“He hasn't made any progress.”
“What about portals, Gwendy?”
“Are you finally getting around to fixing it? Now that thing is janky for your back! I told you this before, Miggy!” Peter flung himself up on the high rise.
Miguel really tried using those breathing methods that you'd taught him, but so far, his nerves were winning. May, as usual, fled from her carrier and swung herself all over the room, screeching with full glee.
“Hey, where did you want us to store the anomaly? Peter here forgot to bring the light cages, though I still find that method of holding them in confinement as if they were animals indecent.”
“Look, I just happened to misplace them; it happens! Hey, are you doing alright there, buddy? Seems as if you’re about to blow a fuse.”
Peter scooted closer to the irritated man, as Miguel did everything in his power to not have an outburst. His muscles strained, his eyes drawn shut, mumbling to himself in Spanish.
Jess apathetically stared, and a hand was planted on her hip. Hobie and Gwen side-eyed each other, curious about how this was going to pan out.
“What were you guys actually discussing, Jess?” Hobie leaned on a nearby steel wall, messing with one of his guitar picks.
Jess was taunting Miguel at this point, unapologetic about this whole situation.
“He was just about to explain the mass of reports and what we were going to do about them. Isn’t that right, Miguel?”
He knew the game she was playing, and he wasn’t trying to join in. Peter approached even closer and bent over to take a look at his friend. “Hey, you’re good. Just say what you have to say.”
“So, are those portals not getting fixed?” Gwen swayed as Miguel’s anger tempted to jump out when he opened his mouth.
Then the lightbulb switched on.
“Gwen!” Miguel accidentally yelled at the young teen.
“Jeez, dude, you don’t have to do all that, but what’s up?”
“How good are you at filling out reports?”
Jess raised an eyebrow, wondering exactly where he was going with this.
“Uh, they’re pretty easy. Just like a high school essay, you’re bullshi-” Miguel narrowed his gaze at the ghost spider before she quickly caught herself. “Summarizing events by making them sound smart and sophisticated. I can do about, let’s see, fifteen in under an hour if the time permits.”
“You’re free from missions for the rest of the week to help Jess catch up on reports. I will also help out if I’m able to. If that's okay with you, Jess?” Miguel eyeballed her, derisiveness in that question.
Jess tongue was in her cheek as she could only roll her eyes. “Yeah.”
“Also, I do have code written up for the device. It’s just in my unique language, so taking notes will be a hassle for Spider-Byte to understand; however, I can make a simple guide for the ones that she is comfortable with. So tell her she can begin with that.”
Jess clicked her tongue and inclined her head. “Alright. I’ll get to her about that. Let’s go, Gwen, and I’ll supply you with a light cage, Hobie. Have a nice day, Peter. Miguel.”
Gwen shrugged her shoulders at the Brit, who nonchalantly joined in with her, as the three made their way out.
May, who was crawling on the desk, was picked up by Peter, stunned by that display, as Miguel’s eyes darted from the PCs to the flabbergasted man, making him sweat.
“Will you stop looking at me that way?!”
“I have never seen you so calmly handle yourself like that before!” Peter joyfully slapped the dented desk a few times.
“So?”
“So? You’re learning how to control your temper! That’s really good for you. Have you been watching meditation videos? I do enjoy those zen ones, especially where you’re in a jungle. Hearing those aggressive caws and shrieks from whatever banshee that is really puts Mayday and I to sleep. Isn’t that right? That’s right, Mayday!”
Mayday cooed as Peter bounced her. Miguel just squinted and shook his head.
“No, none of that weird background noise. Just advice someone gave me to just get help from others.”
Peter scoffed and twisted his face at the background comment, then immediately perked up with a glint in his eye. “It’s that girl, isn’t it? It is! Look at you! How have you two been? Wait, you never told me about that date you went on with her; how did it go?”
Miguel stone-faced Peter, but his enthusiasm was oddly contagious. Miguel thought about the days you two have spent together and how you have given nothing but balance and care. He adores being by your side and wouldn’t have it any other way.
“You’re smiling!” Peter pointed at Miguel’s lips.
“N-no! I’m not smiling.” He replaced whatever crept on him with a disgruntled one.
“No, no, you can’t hide it from me." Peter teased him a bit more before patting his back. "I’m happy for you, bud. You deserve this and many more. I’m glad she can give something that many of us can't.”
Miguel bowed his head in thanks and for the recognition in general.
“Going to see her again?”
“Yes, tonight. Don’t tell anyone. And if something were to happen, I’m directing all calls to Lyla, so I’m letting you know in advance.”
“Yes, sir, captain vampire, sir.” Peter stood tall and saluted.
“Don’t ever say that again unless you want to keep that hand.”
“Right, duly noted. Oh! Time to head on off. Mary is making her famous tacos tonight, and I cannot miss that. See you later, Miguel. Don’t have too much fun now. Yes, they are bundles of joy, but I miss my sleep at times.”
“Peter!”
“Have a good rest of the day! Say bye-bye to Miguel, Mayday!” A gurgled attempt rang from the redhead as Peter ventured down the corridor, his babbling baby talk and May’s squeals dying down.
Miguel groaned out and waited until the only sounds he could hear were the machines and nothing more. He pulled out his phone and immediately began to text you.
‘We’re still on for tonight, mi Luna? Also, tell Ronnie to stop slipping her digital business cards in the boxes. I’m not passing them out at the HQ.’
Several seconds went by when a message from you popped up.
‘Yes, mi Estrella. My place or yours? And I told her. She immediately went into a tirade about how you’re being a bad business wing-partner? How it's profession 101, and you’re a “crappy” employee.’
‘Mines, I want to show you something. AND, tell her to stop saying that I'm working for her!’
An instant reply. ‘Got it. And show me something? What is it? Oh, and Ronnie says, and I quote: “You keep denying your work ethics, and I will have to write you up again, lackey.” You’re on thin ice with her, haha.’
‘It’s something that’s… very special to me. And name one time I’m not. I already passed her two-count warning, yet I still managed to garner more.’
‘Ooh, something special. Well, I’m very honored to see it. And she holds this soft spot for you, which she doesn’t give to many. So consider yourself lucky. I think?’
He imagined you giggling over that.
‘Ay, don’t know if I would, but I don’t want her beating me with that bat, so I guess I’ll just have to accept it. But I’ll come get you later on tonight. I’ll see you then, mi corazón.’
‘You won’t get the weapon. I’ll make sure to put a stop to that! But I'll see you tonight, Miggy. I can’t wait to see you.’
Miguel had a slanted grin and settled the phone next to him. Peeking in the corner, a certain video replayed over and over. He dragged the recording to the middle of the screen, zooming it out.
He bleakly glazed over it, remembering that day so well. A harsh waft dragged from between his lips as his eyes tirelessly drooped as she smiled brighter than any star in the sky.
“Hola, Gabi. No pasa un día sin que te extrañe... I–do you remember that person I was telling you about before? The one where I didn’t know how they would react to all that I'd done? Well, they–they accepted that part of me, and it made me feel so warm. Si, mi osita, just like your favorite polka-dotted, fuzzy socks.”
He gave a weak chuckle before continuing.
“Well, I want you to meet them tonight. I know it’s scary meeting new people; I understand, but don’t worry; this person is very kind and sweet. Si, sweeter than jamoncillo and sticky toffee pudding combined. Si, osita, I know they will like you, maybe even more than me. I promise you two will be—”
Miguel’s words got caught in his throat.
“Would've been the best of friends.”
Rapidly blinking his eyes, he concealed the video in plain sight and went straight to work, trying to occupy his mind.
He found himself getting more frustrated as his own mind constricted him. The last few hours were rough on him, somehow worse than previous times, but when that alarm went off, signifying that it was time to get you, that burden parted halfway but was still attached to him.
Miguel dashed around the HQ, hiding in corners or clawing up the ceilings, sneaking into the giant ventilation systems whenever others passed by.
Rounding the exit he needed, he used his inhuman speed, taking a straight shot to the secret back entrance and portal over to your apartments.
Unbeknownst to him, the spider from earlier swung their way back into Miguel's dreary office, anxiously squeaking his name.
“Mr. Miguel? You in here? I have a very serious question regarding my future love life in this establishment!”
They poked their head through, swishing it back and forth.
“Mr. Miguel? Bleh bleh bleh?”
Stepping further in, they were met with an empty space, with Lyla lazily paying attention to the monitors.
“How does he do this all day? It's only been five minutes, and I'm so bored.”
She flicked around some display footage before scrolling over some social media websites.
“Are you kidding, he isn't here? I just need this simple question answered! They told me he's usually here! What the heck gives?” The spider grumbled and impatiently webbed away.
Lyla jumped at the voice before teleporting around, trying to locate who that exactly was as it faded away.
“Uh, I hope that wasn't important.” Lyla shrugged, returning her partial surveillance to the multiverse before immediately going back to scrolling around the internet.
The spider went around, questioning if anyone had seen Jess. After running back and forth for what seemed like ages, they finally tracked her down near the front lobby.
“Jessica! Mrs. Jessica!” The spider called out and flipped their way to the woman.
Jess dropped her arm from her face and blurred at the person wanting them. “Oh, you're that spider from earlier. Um, you're uh-”
“Spider-Tune. I'm from E-75309, but most people call me Jeni.”
“Right, one of the newer recruits. What's up?” Jess rested her back on the drywall.
Not wanting to delay or build up anticipation, Jeni clapped their hands together. “I was just curious about the dating rules and regulations here at the establishment.”
“You want to… date?” Jess raised an eyebrow.
“Mhm! I want to start dating someone.”
Jess gaped, her eyes casting from side to side, slightly perplexed. “Well, I mean, you can date anyone where you're from. No one is really preventing you.”
She waves a hand over her stomach.
“You know you'll just have to go through the training cou-”
“No, I mean, can I date another spider here in the headquarters? I'm aware I can in my world, but I've been talking to this really, really cute Peter, and I won't lie, I want in on that. So is that allowed, or do I have to jump through some hoops?”
Jess barely batted an eye. This wasn't the first time that question had been evoked. It only informs who carefully studied the guidelines versus who skimmed through them.
“Well, establishing a relationship with another spider is possible only within this dimension, but it's highly unacceptable.”
Jeni cocked their head. “So is that a yes?”
“No.”
“No?”
“Yes.”
Jeni deadpanned as they tried to make sense out of it, making Jess heave out an exasperated sigh.
“If you are striving to date another spider, you may only do it on the grounds in this dimension. Sure, you may visit each other with the watches, but you'll eventually have to cut your losses as different people from different universes cannot intermingle. No merging. I am sure you are aware of that.”
Jeni whined and stamped their feet a few times. Jess wearily observed the spider's mini-tantrum and raised her hands.
“I'm sorry, but we have to enforce these rules to keep us all safe.”
“It’s just–it's so unfair how he gets to do it, but we can't. He gets to leave his job whenever, and he gets to date a spider-person? How typical.”
That caught Jess's ear, a probing look etched on her face. “What spiders are seeing each other? Do you know their names or earth numbers? I just want to make sure they know what they're getting themselves into.”
Jeni bobbed their head furiously. “Uh-huh! It's the big man himself. Just because he's the leader, he thinks he gets to go around and bring a Spider-woman from another dimension to his place, but we can't even do that in our own worlds? Such a double standard!”
Jess went dead silent. Her expression is grim. Then her eyebrows knitted together before morphing into a scornful, incredulous one.
“Oh, you have got to be—did you see him with this Spider-woman? Do you know who she is?”
Jeni yelped at the sudden steely, lividness. “Oh, well no, I haven't personally seen it. But one of my new friends said he sees Miguel with her. I wonder if she's a fresh hire as well.”
“Which friend?” Jess sent a chill down their spine.
“Pri- Pete- uh, E-77793 Peter. He only just tells me he sees them but doesn't go into detail because he's scared he'll get in trouble.”
Jess bit her tongue, both hands now firmly placed on her hips, her eyes leering in a specific direction.
“Alright. Alright. This heffa here really thinks he's... You're dismissed. Thank you for that, and have a good rest of your night.”
Jess turned and began to tread off back into the main hub of the building.
Jeni slack-jawed, their brain baffled at what just unfolded. “Think I got the big boss in trouble. Whoops. Well, don't make the rules if you can't follow them.” They mumbled and strolled off in a different direction.
“Lyla!” Jess stormed towards the elevators, a heated drive in her face.
“What's up? What's the rush?” The A.I. popped up next to her shoulder.
“I need access to the security cameras for all sectors near Miguel's apartment. Now.”
Lyla sucked in her teeth and picked the non-existent lint off her coat. “Ooh, no can do, Jess.”
Jess screeched her steps. “What do you mean you can't? I'm allowed access to all footage when he isn't here, and as far as that spider told me, he's not here. Lyla, I'm not in the mood to be playing these games.”
“No, no, I understand. But that's the thing. He's here; that's why I can't give them to you.”
Jess held back her own exploding temper. “Where is he? I need to speak with him.”
“No point in trying to have a pleasant conversation over tea. He barred himself up in the room. Something about working on an invention or something other.” She stretched her arms before crossing them.
“You can go, Lyla.” Her voice contained nothing but strain and sourness.
“Alright. See ya, Jess.” And with that, she was gone.
Jess rubbed her face and groaned furiously. “I'll have to gather evidence the old-fashioned way.”
She tapped her watch a few times, her eyes deeply fixed on trying to search for a certain spider.
“Alright. I hope you have a lot to say.” Jess rotated her body away from the elevators and out towards the front entrance.
• • •
“You did? Look at you!” You merrily jabbed at his arm.
You and Miguel were snuggling on his mattress, munching down on beef and chicken-flavored empanadas Miguel snagged from the canteen.
“It’s not much of a thing to be excited or proud about. I just wanted you to know I took your advice and it worked out.”
You puffed your cheeks and pouted your lips. “Hey, hey, no. It most definitely is. You’re trying to do more for yourself. You are taking into account what you feel as though you want or need to work on and applying it to situations. So yes, it is something to be proud of and excited about!”
Miguel snorted a bit and shook his head. “Ay dios mío, you sound like Peter.”
"Well, clearly, Peter and I have an eye for an eye. We can see something that you’ll see one day. But for now, we are just… transcending on a different quantum level!”
Miguel choked on his empanada, coughing loudly as spurts of laughter would burst out.
“I-is tha-that what you ca-call it?” He regained his breath and wiped away some tears.
You giggled alongside him, patting his back. “I honestly wasn't expecting that to get you.”
“I wasn't expecting it to get me either.”
He placed his empty container on the floor and scooted until his back hit the wall, wiping his hands on his pajama pants.
You followed suit, tossing your half-eaten fried treat in the take-out box. You both sit in comfortable silence, peace flowing in the air as you face ahead, nearly shoulder to shoulder.
You debated if you should ask about that special thing he wanted to show you, but decided to have him present it whenever he was ready. You were highly curious about it but didn’t want to come off as rude and pry too much. Miguel suddenly flopped his head backward.
“You’re allowed to ask, mi corazón. Even though it’s coming from me, you don’t need to feel as though you have to defer or walk around eggshells.”
“How did you know I was thinking of that? And I’m aware; I just don’t want you fraught or to trouble you.”
“Ay, mi Luna, you are the last person to make me go through those things.” He pulled out a tablet shoved underneath the mattress and handed it to you. “And let’s say it was a hunch on how I knew.”
Your eyes peered down at the dark screen, as the only thing casting was a reflection of you and Miguel. You continued gazing upon him, seeing how his expression dropped solemnly.
“I–there is someone I want you to meet. Someone who was... very dear and close to my heart.”
You figured out who might be, but kept your mouth shut and let him continue.
“I talked about her when we went to the botanical garden that first time, and I think now–now would be the best time for you to get to know her.”
You only nodded, allowing him to take over. As you understood, this must have been difficult for him to do. He inputted a password, and there was a single file on the device. He hesitated for a moment before a choking sob nearly escaped him.
He clicked on the image, and the video began to play. It was of a young girl wearing a football uniform who bore a striking resemblance to Miguel. They were both laughing, her on his shoulders with a cupcake in her hand.
“Hola, mi osita, te extraño muchísimo. Do you remember the person I was telling you about? This is her. Mi Luna, this is Gabriella.”
Even though the room was despondent, you managed to display an enthusiastic wave. “Hi Gabriella, it's so nice to meet you!”
Watching the screen together, you both soberly laugh when she gets icing on his cheek.
“How was she in football?”
“Oh, a beast. She was agile and calculating, always a step ahead of her opponent.”
You darted your eyes up at him before going back to the video.
“She did have moments of playing rough. It wouldn't be a game without her getting at least one penalty, but she would make up for lost time tenfold.”
You grinned. “She sounds like she was the brightest ray of sunshine.”
“It was never a dull day with her, I can tell you that.”
You both continued watching when the video ended and clicked off as you noticed teardrops on the tablet screen. You looked up at Miguel, wiping his eyes and trying to cover them with his hands. You blinked a few times, wanting to hold back your own, but refused and allowed them to fall along with him.
“She was beautiful, Miguel. Is. You–you said she was someone very deep and close to your heart, but I believe she still is. And she will always be as long as she remains in your heart, soul, and mind.”
Miguel tilted his head down and was met with that emphatic smile. You were so compassionate and gentle. Your patience never falters, no matter what. More hot tears splashed down his nose, jaw, and cheeks, and right onto his pants and sheets.
You fully handed him the tablet. When it was in his hands, he hugged it.
He hugged it like it would disappear from his grasp. It would be gone just like that. He trembled as he unclenched his jaw and opened his mouth.
A strangled sob escaped. It was painful, as it took a few heaves, but it eventually flowed out. You rubbed his arm and shoulder, silently weeping with him.
You knew you may never fully understand the pain he's going through, but you knew right now that all he needed was a shoulder to cry on. That you would give him the water he wants and needs to have him grow into that flower that will bring its bloom back.
And Miguel would allow you to give him every drop.
Two strings lie stranded.
Miguel spooned you as you both observed the city and night.
After crying both of your tear ducts dry and cradling each other and the tablet, you two pacified your minds, spending the next hour quiet, cuddling and massaging each other's backs, arms, and shoulders.
“Mi Luna?”
You hummed, nestling more into his warming hold.
“How do you feel about kids? Would you ever have any?”
Your eyes jutted open, and you repositioned yourself so you were looking into his crimson-brown eyes.
“Oh, well. I enjoy being around them. I would like to have some, as they bring joy and all…”
You trailed off, as did your eyes. You felt wrong about this, especially after what he has been and is going through. You didn't think it was the most appropriate thing to delve into.
Miguel noticed your dispirited expression as he cupped your face, rubbing his retracted claw over your soft cheek.
“Corazón, it's okay. I'm asking you. I want to talk about this with you. I know you believe this isn't right, but I'm telling you everything we discuss right now will not hurt me. It'll sting, but I will manage."
Even him speaking those words shocked him.
“Are you sure? I don't want you to feel as if you're required to chat about this.”
“Oye. Ay, te preocupas mucho por mí. Go ahead and finish your answer.”
He knocked his forehead on yours, making you huff and chuckle.
“Okay, okay. I would like to have a pretty big family, but as of now, I think I'll start with one or two. Help me understand the grounding of how it'll go.”
“It makes sense when you lay it out like that.”
You nodded your head as the air suddenly tensed up. Miguel released a spent sigh.
“Ask, mi corazón. I'm not going to get upset or go into a downcast state. I had these thoughts myself if I'm asking you for your opinions and views.”
Squeezing his broad shoulders, you briefly nodded. “Okay, if you say it's okay, it's okay! Well, I know how you feel about kids, but if given the possibility... to have more, how many would you have?”
Miguel looked up at the ceiling, pretending to be deep in thought, before gazing back down. “Like you, I would've wanted a big family. I would want them to be endlessly spawned.”
You beamed at that. “I'm not surprised you would want so many.”
“What's that supposed to mean?” He tickled your sides, making you squeal and fidget.
“Hey! Hey!” You laughed, gently slapping before alluding for him to keep going.
“Let's see, how would you raise your kids? What would you like them to be like?”
"Well, like I said before, kids require a lot of patience, so I'll show them kindness and care. I may have stern moments, but I will want them to understand at their own pace as well. Maybe show more than tell certain actions.”
You rested your head on his chest. “And how would I want them to be? I mean, I have moments where I imagine them to be a certain way, but I know that at the end of the day, they are still their own people. I can introduce activities and hobbies, but it's up to them if they'll like to continue.”
Your eyes wandered. “Maybe we can do things that will become a tradition. Family cooking on certain days, maybe a big trip once or twice a year. Things like that.”
Miguel stroked your back and smiled. “You put a lot of thought into this.”
Squeezing your eyes shut, you could only gleam. “Your turn, mister.”
“Si, si.” He tittered out. “Let's see, I would want them to be able to venture out and face things for themselves. I will still show them the ropes and love, but I'm sure I can push them to the wolves. They'll be fine. It'll be fun.”
You crumpled your face, causing him to crack up. “Joking! Estoy bromeando, lo prometo. But I would want them to strive and work hard towards the goals and aspirations they will have. With a little bit of being thrown into the den.”
“Miggy!” You nudged him with your chin.
“I'm joking! Joking. Yeah. Let's go with that.” He kisses your forehead.
“What's one thing you would want them to inherit from you?” You perked your head in between his pecs.
“Mentally or physically?”
“Both.”
“Well, my intelligence. As you said, I have that big boy brain for science and math.” You both grinned at that. “And physically? I…”
You watched as Miguel slightly dissociated before faintly blinking back. “I–nothing. I'm too much of a… of a–”
“A strong man with beautiful features and incredible powers?”
“Whose body is horribly genetically altered into this giant freak? That has to deal with these abnormalities to keep this body going.”
A boiling force emerged from you. Pressing your forehead into his, that blazing passion you held for him burned through.
“Stop that! You have to take extra stuff to help your body keep flowing, but guess what? Some may need more accommodations than others, but that’s okay. It doesn’t make you any less important or valuable. So, one nice thing! One!”
Miguel was taken aback by your firmness and robust determination. But yet, it was oddly nice to have someone have that drive for him.
“I would like for them to have… my enhanced hearing or sight, or my speeds.”
“Ooh, sight. You do have beautiful eyes. But don't talk down on yourself, or else I’ll kiss you until you conform.”
“It sounds more like a reward than a punishment.” He brushed your hair with his palm.
“It can be a mixture.” You snickered, “But know that you are allowed to show yourself a bit of compassion. I would lie and say I don’t struggle with showing it to myself, but I don’t want to expose myself too much.” You stuck your tongue out.
“You will be a good mom.” Miguel caressed your cheek, making you flustered.
“Uh, uh, your turn.”
“You still have to answer the physical and mental question." A smirk creased the left side of his face.
“My knowledge of random trivia and, um, whatever looks good on me!” You swatted him, wanting to change the subject.
“Your smile.”
Your breath hitched as you tried to hold back that squeal. “Yo-your turn!” You croaked out.
His smirk got even wider.
“Alright, what about baptism?”
“Baptism? I'll be fine with it, but any particular reason?”
“I just don't want my mama crawling out of her grave and beating me with her own casket if I don't. And I'm Irish as well, so I also don't want my ancestors pummeling me with their headstones either.”
A giggle slipped. “That's perfectly understandable.”
“And it's just the baptism part, not so much the ‘pray to the pope,’ Catholic ordeal. Well, only if they want to pray to that old man.”
“I like to think I'm spiritual, but I think I would've weirdly compromised with the religion.”
“Spiritual? Oh wow, I never would've guessed. Nope, none at all.”
You gently nudged his chest a few times and blew a raspberry.
“¡Oye! You're the one who told me you don't mind a good sarcastic remark.” He entrapped his arms around you, bringing you closer to his chest.
You two begin to playfully wrestle, tussling back and forth for a minute, laughter ricocheting off the bedroom walls, until Miguel allows you to pin him down. Sucking in a good amount of air, you both become entranced by one another's gaze.
“How are you feeling?” You glide your hand down the outline of his jawline, feeling the scratchiness from his stubble.
“Now, or in general?” Miguel lulled at your touch.
“Both.”
“Now? I feel content, a sentiment I'm rarely allowed. In general? I don't know. I always think I know what's going on, whether it's inside or all around. That I have everything under control. But now... now I can't say what direction to face.”
“One thing I learned about life is that it can lead you down many paths. You may never know where it can take you. The one you may trail could suddenly take a left, then a sharp right.”
You pecked his cheek and yawned out, nuzzling the top of your head in the crook of his neck. “Life is a funny thing. Some see it as set in stone, but I believe it's not. You can't really put a timestamp on it. Maybe you can change your outcomes, and that itself can lead you down other routes you didn't even think were possible. You can always plan for it, but that doesn't mean it will always fall through.”
There was a hitch in his breath. A sullen uneasiness rushed him internally as his mind jumbled, screeching to him about what he witnessed and about the canon.
But he decided to ignore it.
One day, he would talk to you about the canon and how the timelines work. Yet for now, he was engaging in this itch. The longing and desire for your presence.
The time will unveil itself in all of its glory. But it can wait.
“Mi Estrella?” Your words slurred a bit as you fought to stay awake.
“Oh, sorry, mi Luna, I'm taking in the wisdom you've imparted onto me. I wish I had that type of smarts.”
“Shush. With that enormous brain, you probably have a bazillion amounts of sagacity running through that you may never even know of.”
An exhale of a chortle puffed out from his mouth and nose. “There are so many I'm unaware of. I should probably start looking into that.”
“You definitely should.”
Tranquility befallen them. He loves this. This serenity.
“I just realized something.”
“And what's that, mi Luna?”
“At the botanical garden, you said daisies represent new beginnings.”
“Mhm?”
“And that the moon is also the start of something new. Miguel, did you do that on purpose? Are you saying I'm a new beginning to something?”
Miguel leaned his head down and kissed the crown of your hair.
“Eres el nuevo paso hacia algo que hace mucho que no puedo dar. Gracias, mi Luna. Gracias por todo.”
You couldn't decipher the first half but were able to translate the last.
Thank you. Thank you for everything.
You didn't fully understand why he was thanking you, but you didn't stall on it much longer than you felt like you needed to.
“I... I love you, mi Estrella.” You snuggled up even more somehow, dozing off on his chest, your soft snores flowing in his ears.
Miguel's heart nearly exploded out of his chest.
Did you mean to say that? Surely you didn't as it was probably the drowsiness that crept up talking for you.
Surely you couldn't love him.
So why did he trust and believe those three simple words?
“Mi Luna, mi corazón. Mi tierra, mi cielo, mi universo. Thank you.”
The flames continue to inflame the singular candlestick in the dusky space.
His head is able to slightly raise. Something he wasn't able to do. There, he gets a glimpse. A glimpse of something peculiar; however, it's still shrouded in the bleak void.
What is the flame wanting to show?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
@prozacgooble @ella-janehaven @sanguwuxyoonbummy
#miguel o'hara#miguel x fem!reader#tales the songs weave#miguel x reader#miguel x y/n#miguel x you#atsv miguel#miguel fanfic#miguel spiderverse#miguel o'hara x reader#miguel spiderman#atsv#miguel o'hara x you#miguel o'hara x y/n
29 notes
·
View notes
Text
I stole a page from Wu Xie's private notes because I thought it was pretty.
[CW: insects, tryptophobia, harm to a human]
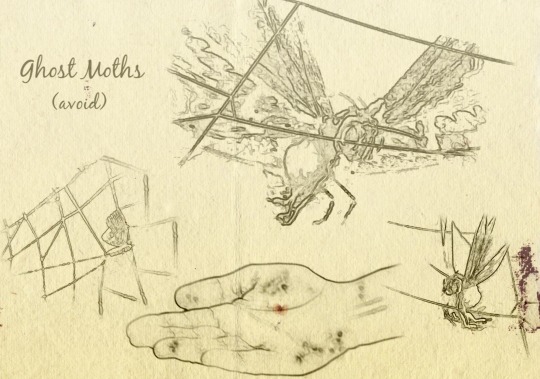
[ID Landscape page showing 'pencil' sketches of a moth and web, some small with folded wings, one large with outspread wings partially drawn in mottled glory. Centre bottom is the sketch of a hand with mysterious pockmarks. There are spots and scrapes of a red-brown substance. Title reads, 'Ghost Moths (avoid)'. End ID]
// Image Credits
Mystic Nine screencaps, heavily edited "Hand, Palm, Fingers" by Alexander Lesnitsky, Pixabay "Nest Wasp Insect" by notre_planete, Pixabay Pixabay stock image (spotted paper)
// Some of the details, in large:

[ID Close-up of spread-winged ghost moth, in bright colours and wide 'brush-strokes' like oil paint. End ID]
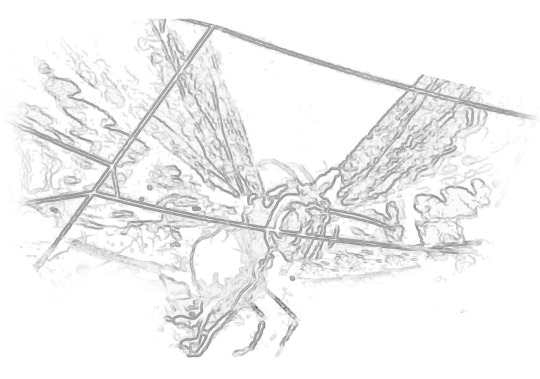
[ID Version of the painted moth, now looking like pencil on a white background. End ID]
I'm not going to say there's not stuff about these edits that isn't insanely nitpicky, frustrating, and tedious, but also a big chunk of this is knowing which filters can be slapped onto what and what effect they might have. The 'pencil' is directly derived from the 'oil' with some clean-up with the eraser tool and then copy-pasting some of the left wing to fill in a gap in the right that didn't convert well (that shadowy bit at the bottom.)
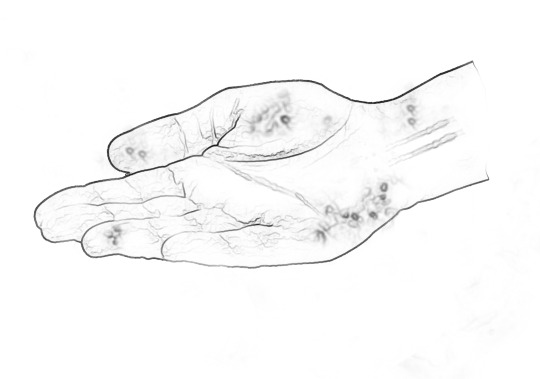
[ID 'Sketch' of a hand held palm up with alarming smudges and small pockmarks dotted all over. End ID]
I got those crater textures by converting a picture of a wasp nest to 'pencil' and pairing it down until I got those alarming circles, and then played around with placement. Also... this started as a photo of a hand but I lost the tendons and the palm crease in conversion and rebuilt them from spare parts.
I'm. I'm pretty sure a real graphic designer would be Very Unimpressed by what passes for technique here, but it gets shit done and certainly entertains me.
[Permission to use or remix these images, with or without credit. (Though namedropping the Pixabay sources would be ace.) Please do fold, spindle, or mutilate...]
4 notes
·
View notes
Text
What is an ISP Proxy?
An ISP Proxy is a type of proxy hosted in a data center but uses residential IP addresses. Through ISP proxies, you can take advantage of the speed of data center networks while benefiting from the good reputation of residential IPs.
If ISP proxies are a combination of data center and residential proxies in some way, we might want to first define these terms.
Data Center Proxies are designed with simplicity in mind. In most cases, traffic is forwarded from the proxy client to the data center, where the provider redirects your traffic to the destination. As a result, the traffic originates from one of the IP addresses in the data center, meaning multiple users often share the same IP address. For anyone trying to block their use, this can be a red flag. The main advantages of data center proxies are speed and network stability, as data center networks are very stable and offer gigabit speeds.
Residential Proxies rely on the ability of an Internet Service Provider (ISP) to assign IP addresses tied to specific locations. In other words, you get a legitimate and unique IP address that masks your actual location.
With ISP proxies, you get access to these legitimate and unique IP ranges, and hosting them in a data center provides an additional benefit. This makes ISP proxies particularly effective, offering the benefits of both residential proxy services (such as the ability to surf the web from anywhere and the good reputation of residential IPs) and data center proxy services (such as impressive speed).
---
Why Do You Need ISP Proxies?
As you can see, ISP proxies combine the undetectable features of residential proxies with the speed of data center proxies. ISP proxy providers achieve this by working with different ISPs to provide IP addresses instead of the user's IP address. This makes them especially useful for various tasks. Let’s take a look at some of them:
1. Web Scraping
ISP proxies are the best choice for web scraping. They provide fast, undetectable connections that allow you to scrape as much data as needed.
2. Bypass Rate Limiting Displayed as Residential Connections
To prevent attacks like Denial of Service (DoS), most websites and data centers implement rate limiting. This prevents a single IP address from making too many requests or downloading too much data from a single website. The direct consequence is that if you perform web scraping, you are likely to hit these limits.
However, ISP proxies offer a way to bypass rate limits; they use ISP IP addresses to trick the rate limiter code, making it appear as if the requests are coming from a different residential location.
3. Accessing Geo-Restricted Content
Like all proxies, ISP proxies allow you to change your location, making it appear as though you are accessing the internet from another country or region.
4. Bulk Purchasing of Limited Edition Products
E-commerce websites take proactive measures to prevent bots (automated scripts) from purchasing products on their platforms. One common technique is to blacklist IP addresses associated with compulsive purchasing behavior. ISP proxies can help you bypass these restrictions.
---
A Closer Look at ISP Proxies
As mentioned earlier, ISP proxies are hosted in data centers and provide internet service provider IP addresses to the destination. Since ISPs own large pools of public IP addresses, it is nearly impossible to trace the computer using the proxy.
While the main benefit is that they are ideal for web scraping, they also provide other features such as:
- Security: End-to-end encryption, firewalls, web filtering, auditing, and analysis.
- Performance: Web caching and high-speed internet from data centers to destinations.
The uniqueness of ISP proxies is that they are the only proxies that directly deal with ISPs to provide the best anonymous connection. While data center proxies are a good option for providing speed and privacy at a lower price, ISP proxies combine the ability to offer speed and anonymity, giving them a significant advantage.
---
Use Cases
The speed and undetectability of ISP proxies make them the preferred choice for large-scale network operations such as web scraping, SEO monitoring, social media monitoring, and ad verification. Let’s take a deeper look at each use case.
1. Web Scraping
Web scraping is the process of analyzing HTML code to extract the required data from websites.
While the concept is simple, large-scale web scraping requires proxy servers to change your location because many websites display different pages based on your location Additionally, to scrape large volumes of data within a reasonable timeframe, proxies need to be extremely fast. Because of these reasons, ISP proxies are considered the best choice for web scraping.
2. SEO Monitoring
SEO monitoring involves checking the performance of your website, content, articles, etc., in search engine results. However, search engine results are influenced by your location, and the cookies attached to your web browser can affect the displayed results. To bypass these issues, proxies are needed to anonymize your connection or simulate a user from another global location.
Moreover, SEO monitoring involves frequent access to the same webpage, which could lead to your IP address being blacklisted or subjected to rate limits. Therefore, it’s best to use proxies when performing SEO monitoring.
3. Social Media Monitoring
Similar to SEO monitoring, activities in social media monitoring can raise suspicion. As a result, you are forced to comply with the host's rules to avoid being blocked or banned from the platform. For example, managing multiple accounts with the same IP address would certainly raise red flags.
In such cases, ISP proxies can be particularly useful because they fool social network algorithms about your IP address, so you won’t be blocked in the end.
4. Ad Verification
As a marketer, you may want to verify that your advertising partners are delivering on their promises and that the statistics they provide are legitimate.
Ad verification involves scanning the web to check if the ads displayed on various websites match campaign standards, appear on the right sites, and reach the target audience. Since these scans need to cover millions of websites, ISP proxies are ideal to ensure that your ad verification process runs quickly and without being blocked due to excessive use of IP addresses.
---
Conclusion
ISP proxies combine the best of both worlds by offering the speed and stability of data center proxies along with the anonymity and legitimacy of residential proxies. This makes them the perfect tool for activities that require speed, anonymity, and high-volume operations, such as web scraping, SEO monitoring, social media management, and ad verification. By working with ISPs to provide legitimate and unique IP addresses, ISP proxies help users bypass restrictions, access geo-restricted content, and operate more efficiently online.
2 notes
·
View notes
Text
In the subject of data analytics, this is the most important concept that everyone needs to understand. The capacity to draw insightful conclusions from data is a highly sought-after talent in today's data-driven environment. In this process, data analytics is essential because it gives businesses the competitive edge by enabling them to find hidden patterns, make informed decisions, and acquire insight. This thorough guide will take you step-by-step through the fundamentals of data analytics, whether you're a business professional trying to improve your decision-making or a data enthusiast eager to explore the world of analytics.
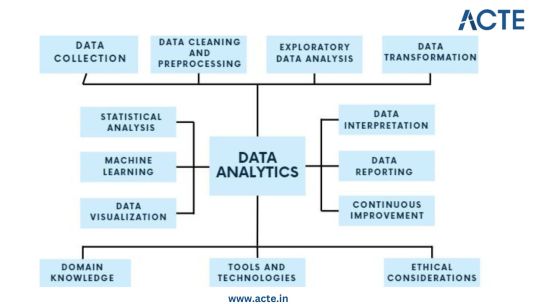
Step 1: Data Collection - Building the Foundation
Identify Data Sources: Begin by pinpointing the relevant sources of data, which could include databases, surveys, web scraping, or IoT devices, aligning them with your analysis objectives. Define Clear Objectives: Clearly articulate the goals and objectives of your analysis to ensure that the collected data serves a specific purpose. Include Structured and Unstructured Data: Collect both structured data, such as databases and spreadsheets, and unstructured data like text documents or images to gain a comprehensive view. Establish Data Collection Protocols: Develop protocols and procedures for data collection to maintain consistency and reliability. Ensure Data Quality and Integrity: Implement measures to ensure the quality and integrity of your data throughout the collection process.
Step 2: Data Cleaning and Preprocessing - Purifying the Raw Material
Handle Missing Values: Address missing data through techniques like imputation to ensure your dataset is complete. Remove Duplicates: Identify and eliminate duplicate entries to maintain data accuracy. Address Outliers: Detect and manage outliers using statistical methods to prevent them from skewing your analysis. Standardize and Normalize Data: Bring data to a common scale, making it easier to compare and analyze. Ensure Data Integrity: Ensure that data remains accurate and consistent during the cleaning and preprocessing phase.
Step 3: Exploratory Data Analysis (EDA) - Understanding the Data
Visualize Data with Histograms, Scatter Plots, etc.: Use visualization tools like histograms, scatter plots, and box plots to gain insights into data distributions and patterns. Calculate Summary Statistics: Compute summary statistics such as means, medians, and standard deviations to understand central tendencies. Identify Patterns and Trends: Uncover underlying patterns, trends, or anomalies that can inform subsequent analysis. Explore Relationships Between Variables: Investigate correlations and dependencies between variables to inform hypothesis testing. Guide Subsequent Analysis Steps: The insights gained from EDA serve as a foundation for guiding the remainder of your analytical journey.
Step 4: Data Transformation - Shaping the Data for Analysis
Aggregate Data (e.g., Averages, Sums): Aggregate data points to create higher-level summaries, such as calculating averages or sums. Create New Features: Generate new features or variables that provide additional context or insights. Encode Categorical Variables: Convert categorical variables into numerical representations to make them compatible with analytical techniques. Maintain Data Relevance: Ensure that data transformations align with your analysis objectives and domain knowledge.
Step 5: Statistical Analysis - Quantifying Relationships
Hypothesis Testing: Conduct hypothesis tests to determine the significance of relationships or differences within the data. Correlation Analysis: Measure correlations between variables to identify how they are related. Regression Analysis: Apply regression techniques to model and predict relationships between variables. Descriptive Statistics: Employ descriptive statistics to summarize data and provide context for your analysis. Inferential Statistics: Make inferences about populations based on sample data to draw meaningful conclusions.
Step 6: Machine Learning - Predictive Analytics
Algorithm Selection: Choose suitable machine learning algorithms based on your analysis goals and data characteristics. Model Training: Train machine learning models using historical data to learn patterns. Validation and Testing: Evaluate model performance using validation and testing datasets to ensure reliability. Prediction and Classification: Apply trained models to make predictions or classify new data. Model Interpretation: Understand and interpret machine learning model outputs to extract insights.
Step 7: Data Visualization - Communicating Insights
Chart and Graph Creation: Create various types of charts, graphs, and visualizations to represent data effectively. Dashboard Development: Build interactive dashboards to provide stakeholders with dynamic views of insights. Visual Storytelling: Use data visualization to tell a compelling and coherent story that communicates findings clearly. Audience Consideration: Tailor visualizations to suit the needs of both technical and non-technical stakeholders. Enhance Decision-Making: Visualization aids decision-makers in understanding complex data and making informed choices.
Step 8: Data Interpretation - Drawing Conclusions and Recommendations
Recommendations: Provide actionable recommendations based on your conclusions and their implications. Stakeholder Communication: Communicate analysis results effectively to decision-makers and stakeholders. Domain Expertise: Apply domain knowledge to ensure that conclusions align with the context of the problem.
Step 9: Continuous Improvement - The Iterative Process
Monitoring Outcomes: Continuously monitor the real-world outcomes of your decisions and predictions. Model Refinement: Adapt and refine models based on new data and changing circumstances. Iterative Analysis: Embrace an iterative approach to data analysis to maintain relevance and effectiveness. Feedback Loop: Incorporate feedback from stakeholders and users to improve analytical processes and models.
Step 10: Ethical Considerations - Data Integrity and Responsibility
Data Privacy: Ensure that data handling respects individuals' privacy rights and complies with data protection regulations. Bias Detection and Mitigation: Identify and mitigate bias in data and algorithms to ensure fairness. Fairness: Strive for fairness and equitable outcomes in decision-making processes influenced by data. Ethical Guidelines: Adhere to ethical and legal guidelines in all aspects of data analytics to maintain trust and credibility.
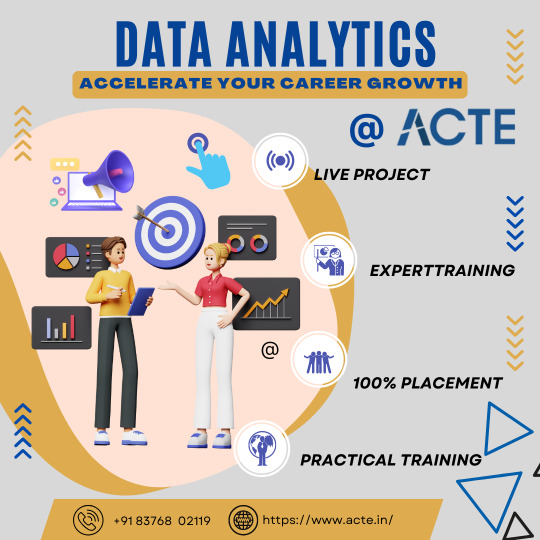
Data analytics is an exciting and profitable field that enables people and companies to use data to make wise decisions. You'll be prepared to start your data analytics journey by understanding the fundamentals described in this guide. To become a skilled data analyst, keep in mind that practice and ongoing learning are essential. If you need help implementing data analytics in your organization or if you want to learn more, you should consult professionals or sign up for specialized courses. The ACTE Institute offers comprehensive data analytics training courses that can provide you the knowledge and skills necessary to excel in this field, along with job placement and certification. So put on your work boots, investigate the resources, and begin transforming.
24 notes
·
View notes
Text
Key Programming Languages Every Ethical Hacker Should Know
In the realm of cybersecurity, ethical hacking stands as a critical line of defense against cyber threats. Ethical hackers use their skills to identify vulnerabilities and prevent malicious attacks. To be effective in this role, a strong foundation in programming is essential. Certain programming languages are particularly valuable for ethical hackers, enabling them to develop tools, scripts, and exploits. This blog post explores the most important programming languages for ethical hackers and how these skills are integrated into various training programs.
Python: The Versatile Tool
Python is often considered the go-to language for ethical hackers due to its versatility and ease of use. It offers a wide range of libraries and frameworks that simplify tasks like scripting, automation, and data analysis. Python’s readability and broad community support make it a popular choice for developing custom security tools and performing various hacking tasks. Many top Ethical Hacking Course institutes incorporate Python into their curriculum because it allows students to quickly grasp the basics and apply their knowledge to real-world scenarios. In an Ethical Hacking Course, learning Python can significantly enhance your ability to automate tasks and write scripts for penetration testing. Its extensive libraries, such as Scapy for network analysis and Beautiful Soup for web scraping, can be crucial for ethical hacking projects.
JavaScript: The Web Scripting Language
JavaScript is indispensable for ethical hackers who focus on web security. It is the primary language used in web development and can be leveraged to understand and exploit vulnerabilities in web applications. By mastering JavaScript, ethical hackers can identify issues like Cross-Site Scripting (XSS) and develop techniques to mitigate such risks. An Ethical Hacking Course often covers JavaScript to help students comprehend how web applications work and how attackers can exploit JavaScript-based vulnerabilities. Understanding this language enables ethical hackers to perform more effective security assessments on websites and web applications.
Biggest Cyber Attacks in the World
youtube
C and C++: Low-Level Mastery
C and C++ are essential for ethical hackers who need to delve into low-level programming and system vulnerabilities. These languages are used to develop software and operating systems, making them crucial for understanding how exploits work at a fundamental level. Mastery of C and C++ can help ethical hackers identify and exploit buffer overflows, memory corruption, and other critical vulnerabilities. Courses at leading Ethical Hacking Course institutes frequently include C and C++ programming to provide a deep understanding of how software vulnerabilities can be exploited. Knowledge of these languages is often a prerequisite for advanced penetration testing and vulnerability analysis.
Bash Scripting: The Command-Line Interface
Bash scripting is a powerful tool for automating tasks on Unix-based systems. It allows ethical hackers to write scripts that perform complex sequences of commands, making it easier to conduct security audits and manage multiple tasks efficiently. Bash scripting is particularly useful for creating custom tools and automating repetitive tasks during penetration testing. An Ethical Hacking Course that offers job assistance often emphasizes the importance of Bash scripting, as it is a fundamental skill for many security roles. Being proficient in Bash can streamline workflows and improve efficiency when working with Linux-based systems and tools.
SQL: Database Security Insights
Structured Query Language (SQL) is essential for ethical hackers who need to assess and secure databases. SQL injection is a common attack vector used to exploit vulnerabilities in web applications that interact with databases. By understanding SQL, ethical hackers can identify and prevent SQL injection attacks and assess the security of database systems. Incorporating SQL into an Ethical Hacking Course can provide students with a comprehensive understanding of database security and vulnerability management. This knowledge is crucial for performing thorough security assessments and ensuring robust protection against database-related attacks.
Understanding Course Content and Fees
When choosing an Ethical Hacking Course, it’s important to consider how well the program covers essential programming languages. Courses offered by top Ethical Hacking Course institutes should provide practical, hands-on training in Python, JavaScript, C/C++, Bash scripting, and SQL. Additionally, the course fee can vary depending on the institute and the comprehensiveness of the program. Investing in a high-quality course that covers these programming languages and offers practical experience can significantly enhance your skills and employability in the cybersecurity field.
Certification and Career Advancement
Obtaining an Ethical Hacking Course certification can validate your expertise and improve your career prospects. Certifications from reputable institutes often include components related to the programming languages discussed above. For instance, certifications may test your ability to write scripts in Python or perform SQL injection attacks. By securing an Ethical Hacking Course certification, you demonstrate your proficiency in essential programming languages and your readiness to tackle complex security challenges. Mastering the right programming languages is crucial for anyone pursuing a career in ethical hacking. Python, JavaScript, C/C++, Bash scripting, and SQL each play a unique role in the ethical hacking landscape, providing the tools and knowledge needed to identify and address security vulnerabilities. By choosing a top Ethical Hacking Course institute that covers these languages and investing in a course that offers practical training and job assistance, you can position yourself for success in this dynamic field. With the right skills and certification, you’ll be well-equipped to tackle the evolving challenges of cybersecurity and contribute to protecting critical digital assets.
3 notes
·
View notes
Text
#proxies#proxy#proxyserver#residential proxy#captcha#web scraping techniques#web scraping tools#web scraping services#datascience#data analytics#automation#algorithm
0 notes
Text
Zillow Scraping Mastery: Advanced Techniques Revealed

In the ever-evolving landscape of data acquisition, Zillow stands tall as a treasure trove of valuable real estate information. From property prices to market trends, Zillow's extensive database holds a wealth of insights for investors, analysts, and researchers alike. However, accessing this data at scale requires more than just a basic understanding of web scraping techniques. It demands mastery of advanced methods tailored specifically for Zillow's unique structure and policies. In this comprehensive guide, we delve into the intricacies of Zillow scraping, unveiling advanced techniques to empower data enthusiasts in their quest for valuable insights.
Understanding the Zillow Scraper Landscape
Before diving into advanced techniques, it's crucial to grasp the landscape of zillow scraper. As a leading real estate marketplace, Zillow is equipped with robust anti-scraping measures to protect its data and ensure fair usage. These measures include rate limiting, CAPTCHA challenges, and dynamic page rendering, making traditional scraping approaches ineffective. To navigate this landscape successfully, aspiring scrapers must employ sophisticated strategies tailored to bypass these obstacles seamlessly.
Advanced Techniques Unveiled
User-Agent Rotation: One of the most effective ways to evade detection is by rotating User-Agent strings. Zillow's anti-scraping mechanisms often target commonly used User-Agent identifiers associated with popular scraping libraries. By rotating through a diverse pool of User-Agent strings mimicking legitimate browser traffic, scrapers can significantly reduce the risk of detection and maintain uninterrupted data access.
IP Rotation and Proxies: Zillow closely monitors IP addresses to identify and block suspicious scraping activities. To counter this, employing a robust proxy rotation system becomes indispensable. By routing requests through a pool of diverse IP addresses, scrapers can distribute traffic evenly and mitigate the risk of IP bans. Additionally, utilizing residential proxies offers the added advantage of mimicking genuine user behavior, further enhancing scraping stealth.
Session Persistence: Zillow employs session-based authentication to track user interactions and identify potential scrapers. Implementing session persistence techniques, such as maintaining persistent cookies and managing session tokens, allows scrapers to simulate continuous user engagement. By emulating authentic browsing patterns, scrapers can evade detection more effectively and ensure prolonged data access.
JavaScript Rendering: Zillow's dynamic web pages rely heavily on client-side JavaScript to render content dynamically. Traditional scraping approaches often fail to capture dynamically generated data, leading to incomplete or inaccurate results. Leveraging headless browser automation frameworks, such as Selenium or Puppeteer, enables scrapers to execute JavaScript code dynamically and extract fully rendered content accurately. This advanced technique ensures comprehensive data coverage across Zillow's dynamic pages, empowering scrapers with unparalleled insights.
Data Parsing and Extraction: Once data is retrieved from Zillow's servers, efficient parsing and extraction techniques are essential to transform raw HTML content into structured data formats. Utilizing robust parsing libraries, such as BeautifulSoup or Scrapy, facilitates seamless extraction of relevant information from complex web page structures. Advanced XPath or CSS selectors further streamline the extraction process, enabling scrapers to target specific elements with precision and extract valuable insights efficiently.
Ethical Considerations and Compliance
While advanced scraping techniques offer unparalleled access to valuable data, it's essential to uphold ethical standards and comply with Zillow's terms of service. Scrapers must exercise restraint and avoid overloading Zillow's servers with excessive requests, as this may disrupt service for genuine users and violate platform policies. Additionally, respecting robots.txt directives and adhering to rate limits demonstrates integrity and fosters a sustainable scraping ecosystem beneficial to all stakeholders.
Conclusion
In the realm of data acquisition, mastering advanced scraping techniques is paramount for unlocking the full potential of platforms like Zillow. By employing sophisticated strategies tailored to bypass anti-scraping measures seamlessly, data enthusiasts can harness the wealth of insights hidden within Zillow's vast repository of real estate data. However, it's imperative to approach scraping ethically and responsibly, ensuring compliance with platform policies and fostering a mutually beneficial scraping ecosystem. With these advanced techniques at their disposal, aspiring scrapers can embark on a journey of exploration and discovery, unraveling valuable insights to inform strategic decisions and drive innovation in the real estate industry.
2 notes
·
View notes
Text
25 Python Projects to Supercharge Your Job Search in 2024

Introduction: In the competitive world of technology, a strong portfolio of practical projects can make all the difference in landing your dream job. As a Python enthusiast, building a diverse range of projects not only showcases your skills but also demonstrates your ability to tackle real-world challenges. In this blog post, we'll explore 25 Python projects that can help you stand out and secure that coveted position in 2024.
1. Personal Portfolio Website
Create a dynamic portfolio website that highlights your skills, projects, and resume. Showcase your creativity and design skills to make a lasting impression.
2. Blog with User Authentication
Build a fully functional blog with features like user authentication and comments. This project demonstrates your understanding of web development and security.
3. E-Commerce Site
Develop a simple online store with product listings, shopping cart functionality, and a secure checkout process. Showcase your skills in building robust web applications.
4. Predictive Modeling
Create a predictive model for a relevant field, such as stock prices, weather forecasts, or sales predictions. Showcase your data science and machine learning prowess.
5. Natural Language Processing (NLP)
Build a sentiment analysis tool or a text summarizer using NLP techniques. Highlight your skills in processing and understanding human language.
6. Image Recognition
Develop an image recognition system capable of classifying objects. Demonstrate your proficiency in computer vision and deep learning.
7. Automation Scripts
Write scripts to automate repetitive tasks, such as file organization, data cleaning, or downloading files from the internet. Showcase your ability to improve efficiency through automation.
8. Web Scraping
Create a web scraper to extract data from websites. This project highlights your skills in data extraction and manipulation.
9. Pygame-based Game
Develop a simple game using Pygame or any other Python game library. Showcase your creativity and game development skills.
10. Text-based Adventure Game
Build a text-based adventure game or a quiz application. This project demonstrates your ability to create engaging user experiences.
11. RESTful API
Create a RESTful API for a service or application using Flask or Django. Highlight your skills in API development and integration.
12. Integration with External APIs
Develop a project that interacts with external APIs, such as social media platforms or weather services. Showcase your ability to integrate diverse systems.
13. Home Automation System
Build a home automation system using IoT concepts. Demonstrate your understanding of connecting devices and creating smart environments.
14. Weather Station
Create a weather station that collects and displays data from various sensors. Showcase your skills in data acquisition and analysis.
15. Distributed Chat Application
Build a distributed chat application using a messaging protocol like MQTT. Highlight your skills in distributed systems.
16. Blockchain or Cryptocurrency Tracker
Develop a simple blockchain or a cryptocurrency tracker. Showcase your understanding of blockchain technology.
17. Open Source Contributions
Contribute to open source projects on platforms like GitHub. Demonstrate your collaboration and teamwork skills.
18. Network or Vulnerability Scanner
Build a network or vulnerability scanner to showcase your skills in cybersecurity.
19. Decentralized Application (DApp)
Create a decentralized application using a blockchain platform like Ethereum. Showcase your skills in developing applications on decentralized networks.
20. Machine Learning Model Deployment
Deploy a machine learning model as a web service using frameworks like Flask or FastAPI. Demonstrate your skills in model deployment and integration.
21. Financial Calculator
Build a financial calculator that incorporates relevant mathematical and financial concepts. Showcase your ability to create practical tools.
22. Command-Line Tools
Develop command-line tools for tasks like file manipulation, data processing, or system monitoring. Highlight your skills in creating efficient and user-friendly command-line applications.
23. IoT-Based Health Monitoring System
Create an IoT-based health monitoring system that collects and analyzes health-related data. Showcase your ability to work on projects with social impact.
24. Facial Recognition System
Build a facial recognition system using Python and computer vision libraries. Showcase your skills in biometric technology.
25. Social Media Dashboard
Develop a social media dashboard that aggregates and displays data from various platforms. Highlight your skills in data visualization and integration.
Conclusion: As you embark on your job search in 2024, remember that a well-rounded portfolio is key to showcasing your skills and standing out from the crowd. These 25 Python projects cover a diverse range of domains, allowing you to tailor your portfolio to match your interests and the specific requirements of your dream job.
If you want to know more, Click here:https://analyticsjobs.in/question/what-are-the-best-python-projects-to-land-a-great-job-in-2024/
#python projects#top python projects#best python projects#analytics jobs#python#coding#programming#machine learning
2 notes
·
View notes
Text
Tapping into Fresh Insights: Kroger Grocery Data Scraping
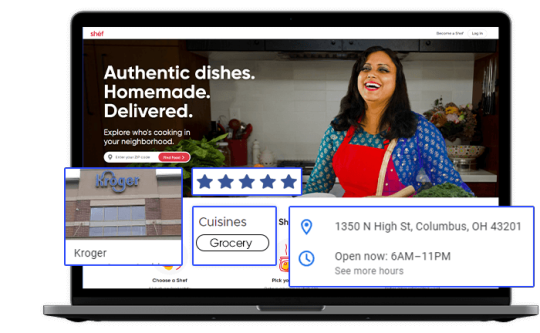
In today's data-driven world, the retail grocery industry is no exception when it comes to leveraging data for strategic decision-making. Kroger, one of the largest supermarket chains in the United States, offers a wealth of valuable data related to grocery products, pricing, customer preferences, and more. Extracting and harnessing this data through Kroger grocery data scraping can provide businesses and individuals with a competitive edge and valuable insights. This article explores the significance of grocery data extraction from Kroger, its benefits, and the methodologies involved.
The Power of Kroger Grocery Data
Kroger's extensive presence in the grocery market, both online and in physical stores, positions it as a significant source of data in the industry. This data is invaluable for a variety of stakeholders:
Kroger: The company can gain insights into customer buying patterns, product popularity, inventory management, and pricing strategies. This information empowers Kroger to optimize its product offerings and enhance the shopping experience.
Grocery Brands: Food manufacturers and brands can use Kroger's data to track product performance, assess market trends, and make informed decisions about product development and marketing strategies.
Consumers: Shoppers can benefit from Kroger's data by accessing information on product availability, pricing, and customer reviews, aiding in making informed purchasing decisions.
Benefits of Grocery Data Extraction from Kroger
Market Understanding: Extracted grocery data provides a deep understanding of the grocery retail market. Businesses can identify trends, competition, and areas for growth or diversification.
Product Optimization: Kroger and other retailers can optimize their product offerings by analyzing customer preferences, demand patterns, and pricing strategies. This data helps enhance inventory management and product selection.
Pricing Strategies: Monitoring pricing data from Kroger allows businesses to adjust their pricing strategies in response to market dynamics and competitor moves.
Inventory Management: Kroger grocery data extraction aids in managing inventory effectively, reducing waste, and improving supply chain operations.
Methodologies for Grocery Data Extraction from Kroger
To extract grocery data from Kroger, individuals and businesses can follow these methodologies:
Authorization: Ensure compliance with Kroger's terms of service and legal regulations. Authorization may be required for data extraction activities, and respecting privacy and copyright laws is essential.
Data Sources: Identify the specific data sources you wish to extract. Kroger's data encompasses product listings, pricing, customer reviews, and more.
Web Scraping Tools: Utilize web scraping tools, libraries, or custom scripts to extract data from Kroger's website. Common tools include Python libraries like BeautifulSoup and Scrapy.
Data Cleansing: Cleanse and structure the scraped data to make it usable for analysis. This may involve removing HTML tags, formatting data, and handling missing or inconsistent information.
Data Storage: Determine where and how to store the scraped data. Options include databases, spreadsheets, or cloud-based storage.
Data Analysis: Leverage data analysis tools and techniques to derive actionable insights from the scraped data. Visualization tools can help present findings effectively.
Ethical and Legal Compliance: Scrutinize ethical and legal considerations, including data privacy and copyright. Engage in responsible data extraction that aligns with ethical standards and regulations.
Scraping Frequency: Exercise caution regarding the frequency of scraping activities to prevent overloading Kroger's servers or causing disruptions.
Conclusion
Kroger grocery data scraping opens the door to fresh insights for businesses, brands, and consumers in the grocery retail industry. By harnessing Kroger's data, retailers can optimize their product offerings and pricing strategies, while consumers can make more informed shopping decisions. However, it is crucial to prioritize ethical and legal considerations, including compliance with Kroger's terms of service and data privacy regulations. In the dynamic landscape of grocery retail, data is the key to unlocking opportunities and staying competitive. Grocery data extraction from Kroger promises to deliver fresh perspectives and strategic advantages in this ever-evolving industry.
#grocerydatascraping#restaurant data scraping#food data scraping services#food data scraping#fooddatascrapingservices#zomato api#web scraping services#grocerydatascrapingapi#restaurantdataextraction
4 notes
·
View notes
Text
Amazon Product Review Data Scraping | Scrape Amazon Product Review Data

In the vast ocean of e-commerce, Amazon stands as an undisputed titan, housing millions of products and catering to the needs of countless consumers worldwide. Amidst this plethora of offerings, product reviews serve as guiding stars, illuminating the path for prospective buyers. Harnessing the insights embedded within these reviews can provide businesses with a competitive edge, offering invaluable market intelligence and consumer sentiment analysis.
In the realm of data acquisition, web scraping emerges as a potent tool, empowering businesses to extract structured data from the labyrinthine expanse of the internet. When it comes to Amazon product review data scraping, this technique becomes particularly indispensable, enabling businesses to glean actionable insights from the vast repository of customer feedback.
Understanding Amazon Product Review Data Scraping
Amazon product review data scraping involves the automated extraction of reviews, ratings, and associated metadata from Amazon product pages. This process typically entails utilizing web scraping tools or custom scripts to navigate through product listings, access review sections, and extract relevant information systematically.
The Components of Amazon Product Review Data:
Review Text: The core content of the review, containing valuable insights, opinions, and feedback from customers regarding their experience with the product.
Rating: The numerical or star-based rating provided by the reviewer, offering a quick glimpse into the overall satisfaction level associated with the product.
Reviewer Information: Details such as the reviewer's username, profile information, and sometimes demographic data, which can be leveraged for segmentation and profiling purposes.
Review Date: The timestamp indicating when the review was posted, aiding in trend analysis and temporal assessment of product performance.
The Benefits of Amazon Product Review Data Scraping
1. Market Research and Competitive Analysis:
By systematically scraping Amazon product reviews, businesses can gain profound insights into market trends, consumer preferences, and competitor performance. Analyzing the sentiment expressed in reviews can unveil strengths, weaknesses, opportunities, and threats within the market landscape, guiding strategic decision-making processes.
2. Product Enhancement and Innovation:
Customer feedback serves as a treasure trove of suggestions and improvement opportunities. By aggregating and analyzing product reviews at scale, businesses can identify recurring themes, pain points, and feature requests, thus informing product enhancement strategies and fostering innovation.
3. Reputation Management:
Proactively monitoring and addressing customer feedback on Amazon can be instrumental in maintaining a positive brand image. Through sentiment analysis and sentiment-based alerts derived from scraped reviews, businesses can swiftly identify and mitigate potential reputation risks, thereby safeguarding brand equity.
4. Pricing and Promotion Strategies:
Analyzing Amazon product reviews can provide valuable insights into perceived product value, price sensitivity, and the effectiveness of promotional campaigns. By correlating review sentiments with pricing fluctuations and promotional activities, businesses can refine their pricing strategies and promotional tactics for optimal market positioning.
Ethical Considerations and Best Practices
While Amazon product review data scraping offers immense potential, it's crucial to approach it ethically and responsibly. Adhering to Amazon's terms of service and respecting user privacy are paramount. Businesses should also exercise caution to ensure compliance with relevant data protection regulations, such as the GDPR.
Moreover, the use of scraped data should be guided by principles of transparency and accountability. Clearly communicating data collection practices and obtaining consent whenever necessary fosters trust and credibility.
Conclusion
Amazon product review data scraping unlocks a wealth of opportunities for businesses seeking to gain a competitive edge in the dynamic e-commerce landscape. By harnessing the power of automated data extraction and analysis, businesses can unearth actionable insights, drive informed decision-making, and cultivate stronger relationships with their customers. However, it's imperative to approach data scraping with integrity, prioritizing ethical considerations and compliance with regulatory frameworks. Embraced judiciously, Amazon product review data scraping can be a catalyst for innovation, growth, and sustainable business success in the digital age.
3 notes
·
View notes
Text
Using indeed jobs data for business
The Indeed scraper is a powerful tool that allows you to extract job listings and associated details from the indeed.com job search website. Follow these steps to use the scraper effectively:
1. Understanding the Purpose:
The Indeed scraper is used to gather job data for analysis, research, lead generation, or other purposes.
It uses web scraping techniques to navigate through search result pages, extract job listings, and retrieve relevant information like job titles, companies, locations, salaries, and more.
2. Why Scrape Indeed.com:
There are various use cases for an Indeed jobs scraper, including:
Job Market Research
Competitor Analysis
Company Research
Salary Benchmarking
Location-Based Insights
Lead Generation
CRM Enrichment
Marketplace Insights
Career Planning
Content Creation
Consulting Services
3. Accessing the Indeed Scraper:
Go to the indeed.com website.
Search for jobs using filters like job title, company name, and location to narrow down your target job listings.
Copy the URL from the address bar after performing your search. This URL contains your search criteria and results.
4. Using the Apify Platform:
Visit the Indeed job scraper page
Click on the “Try for free” button to access the scraper.
5. Setting up the Scraper:
In the Apify platform, you’ll be prompted to configure the scraper:
Insert the search URL you copied from indeed.com in step 3.
Enter the number of job listings you want to scrape.
Select a residential proxy from your country. This helps you avoid being blocked by the website due to excessive requests.
Click the “Start” button to begin the scraping process.
6. Running the Scraper:
The scraper will start extracting job data based on your search criteria.
It will navigate through search result pages, gather job listings, and retrieve details such as job titles, companies, locations, salaries, and more.
When the scraping process is complete, click the “Export” button in the Apify platform.
You can choose to download the dataset in various formats, such as JSON, HTML, CSV, or Excel, depending on your preferences.
8. Review and Utilize Data:
Open the downloaded data file to view and analyze the extracted job listings and associated details.
You can use this data for your intended purposes, such as market research, competitor analysis, or lead generation.
9. Scraper Options:
The scraper offers options for specifying the job search URL and choosing a residential proxy. Make sure to configure these settings according to your requirements.
10. Sample Output: — You can expect the output data to include job details, company information, and other relevant data, depending on your chosen settings.
By following these steps, you can effectively use the Indeed scraper to gather job data from indeed.com for your specific needs, whether it’s for research, business insights, or personal career planning.
2 notes
·
View notes